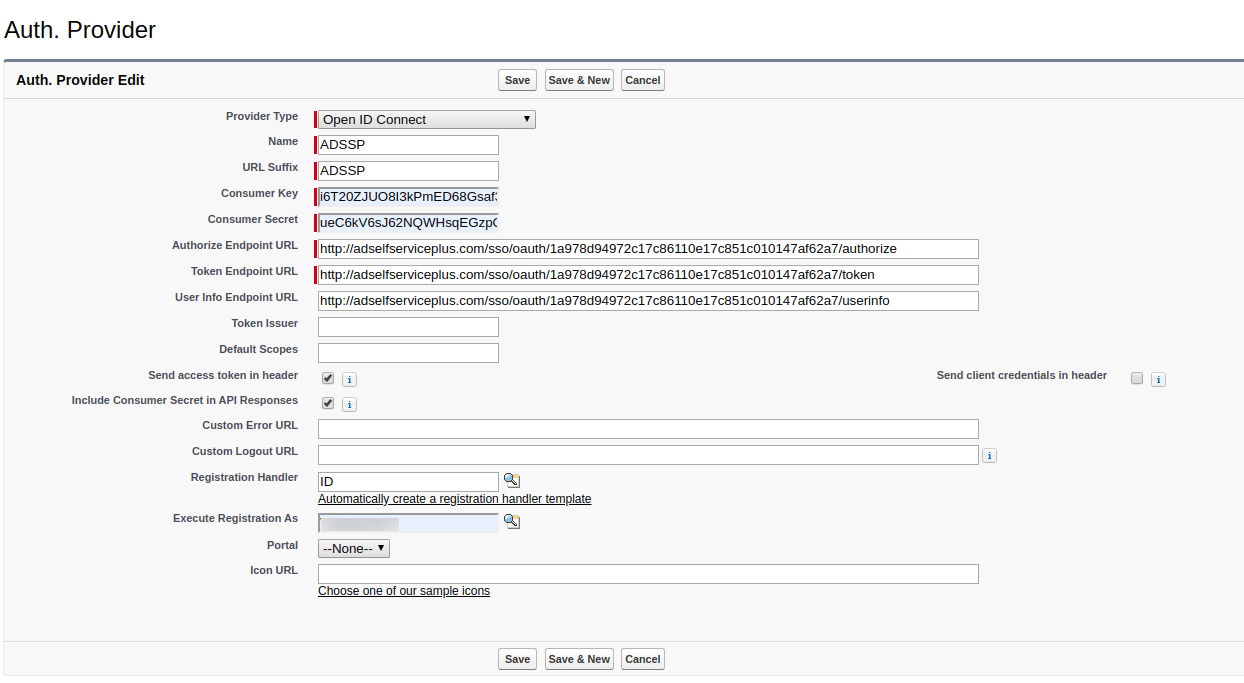
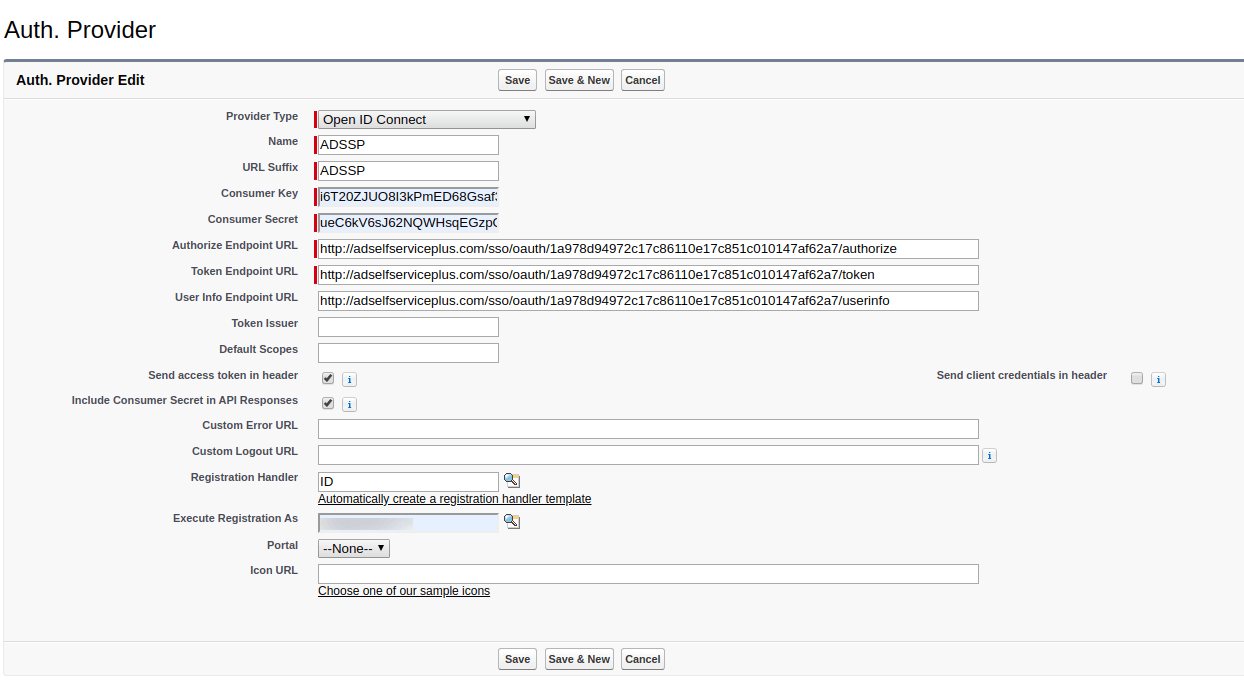
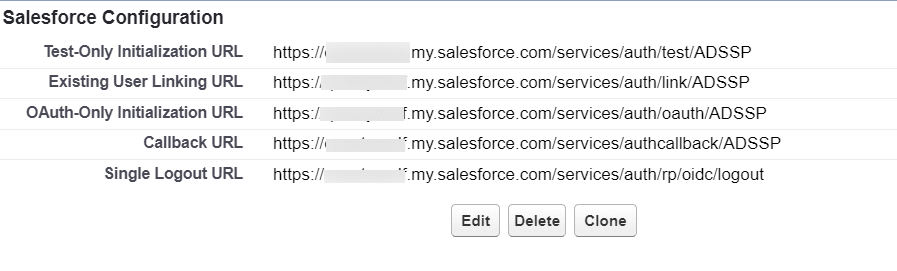
These steps show you how to configure the single sign-on (SSO) functionality using OpenID Connect between ManageEngine ADSelfService Plus and Salesforce.
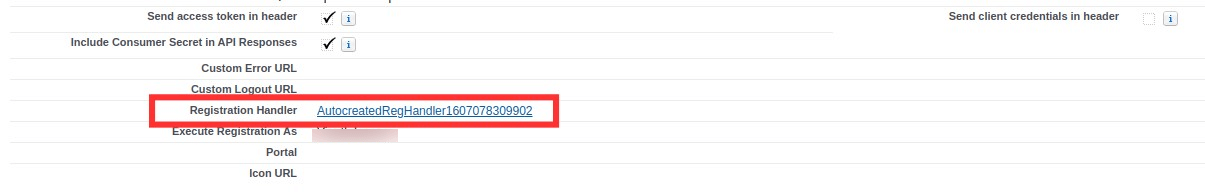
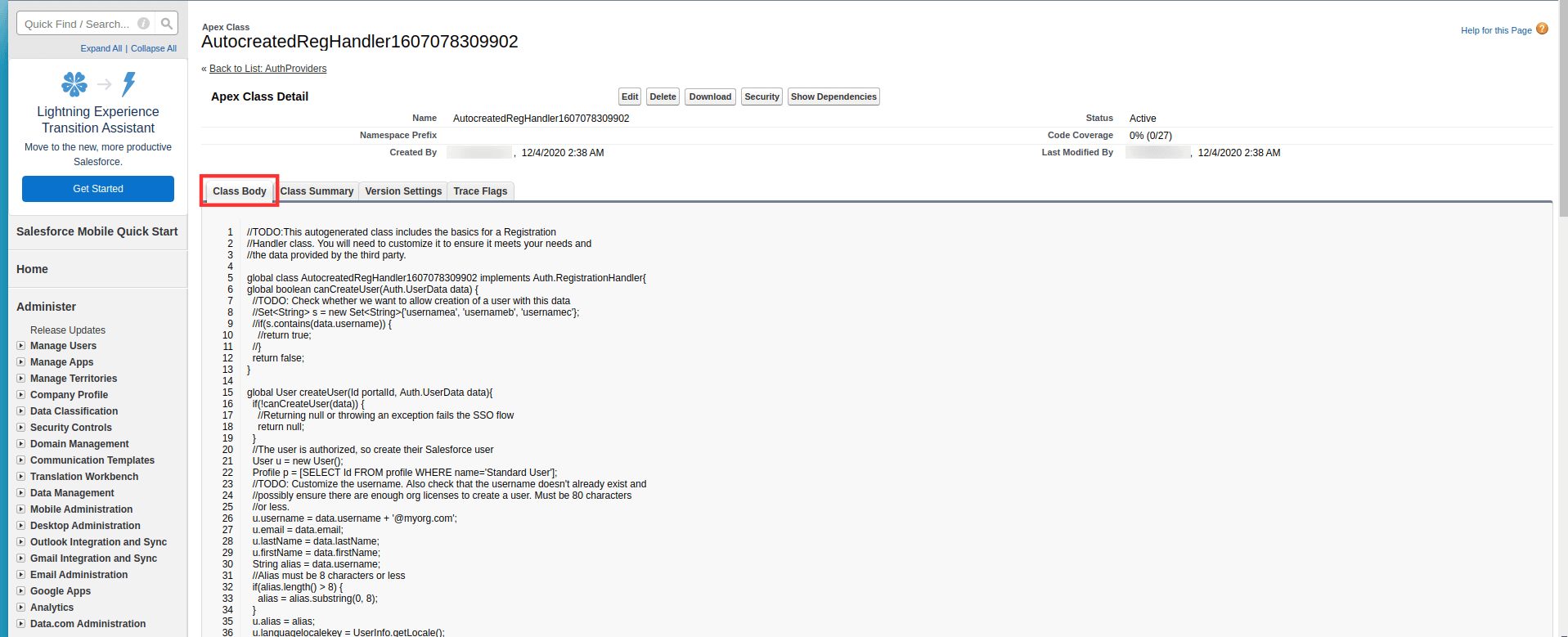
global class IDMPOIDCHandler implements Auth.RegistrationHandler{
global User createUser(Id portalId, Auth.UserData data){
//The user is authorized, so create their Salesforce user
User u = new User();
String username = data.email;
List
if(userList != null && userList.size() > 0) {
u = userList.get(0);
}
return u;
}
global void updateUser(Id userId, Id portalId, Auth.UserData data){
User u = new User(id=userId);
update(u);
}
}
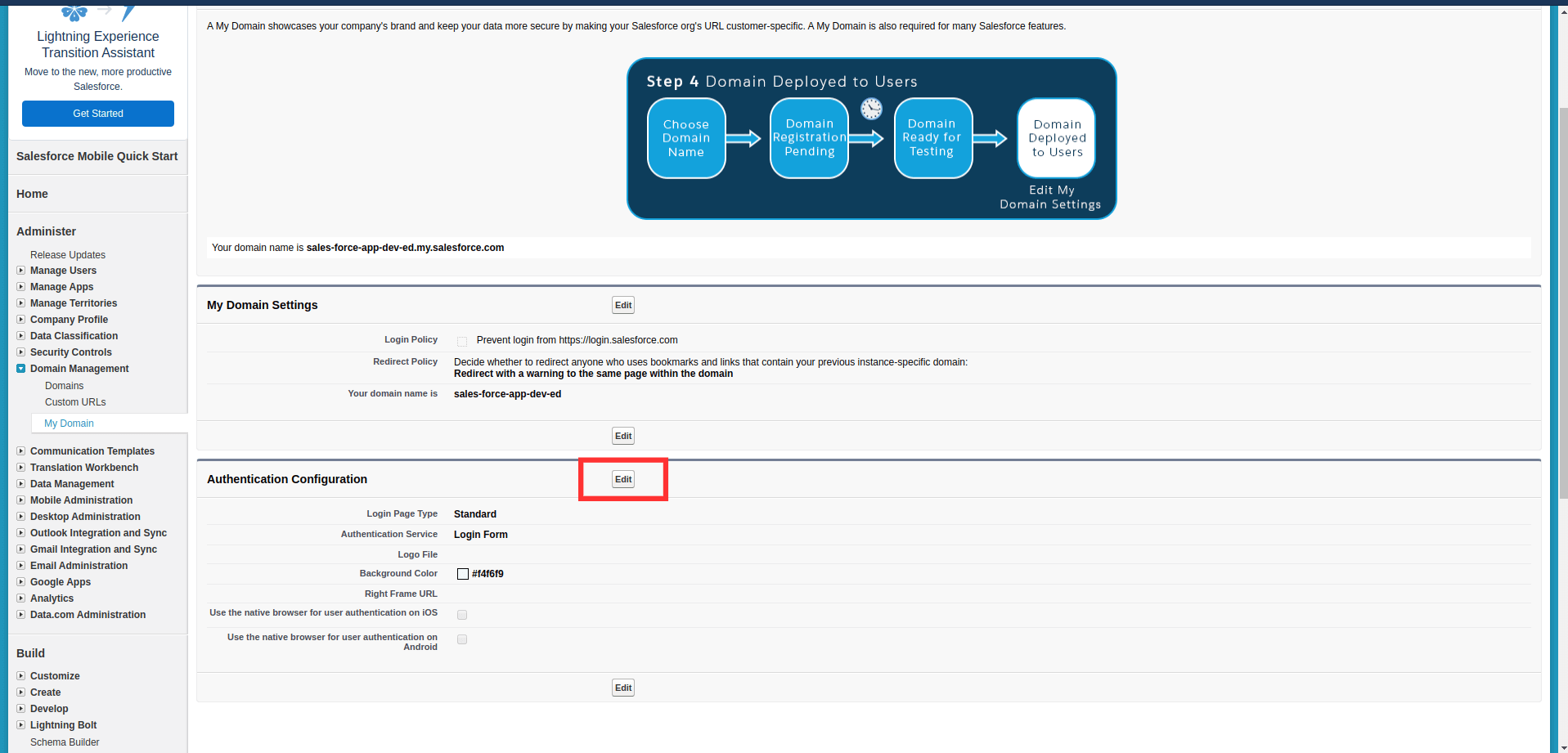
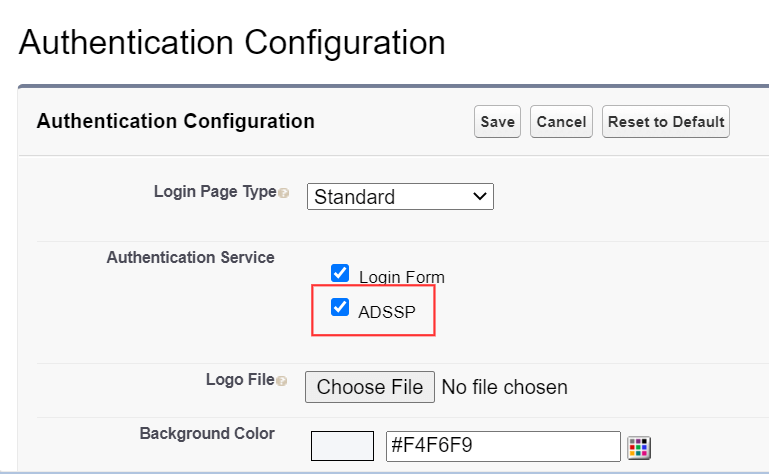
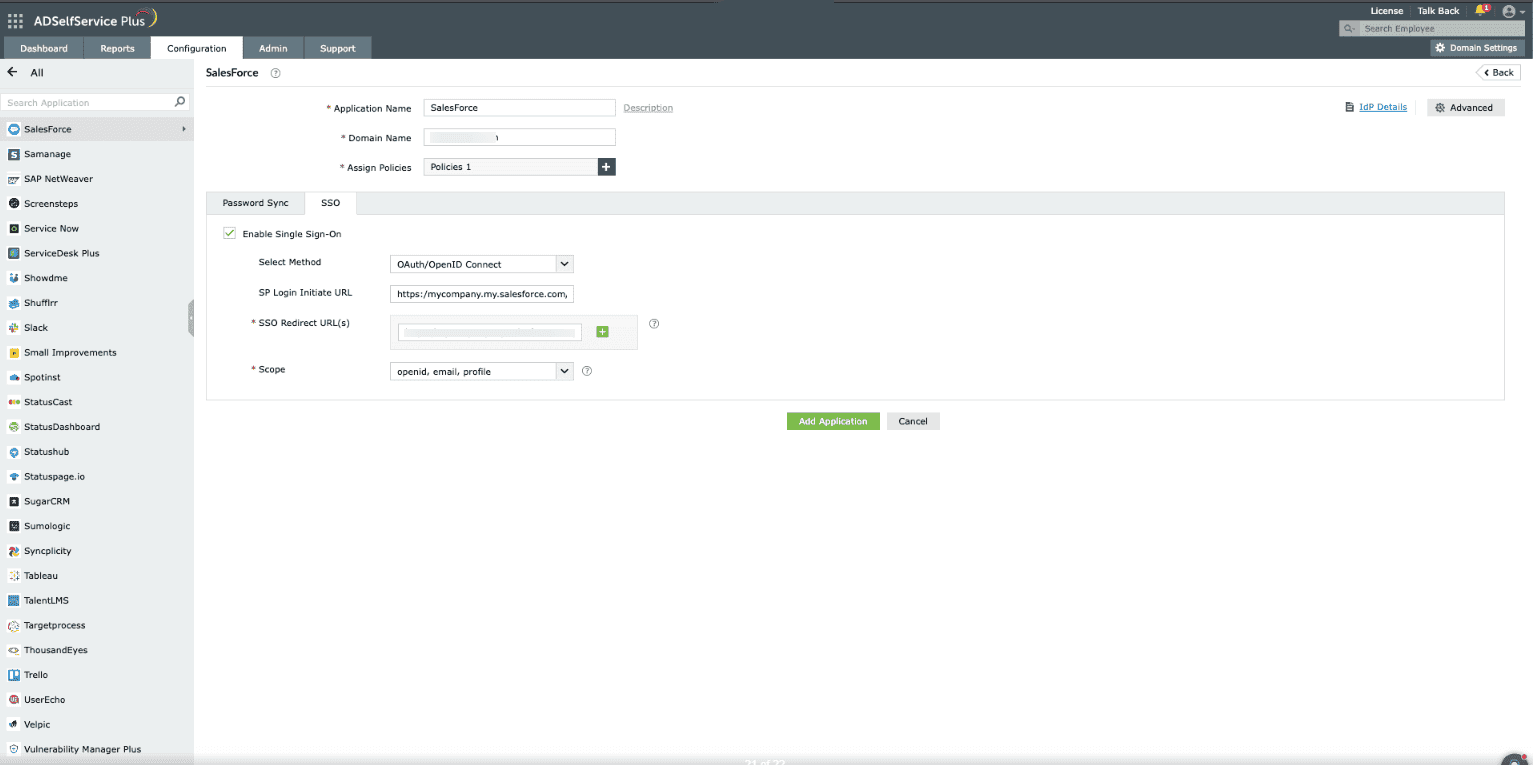
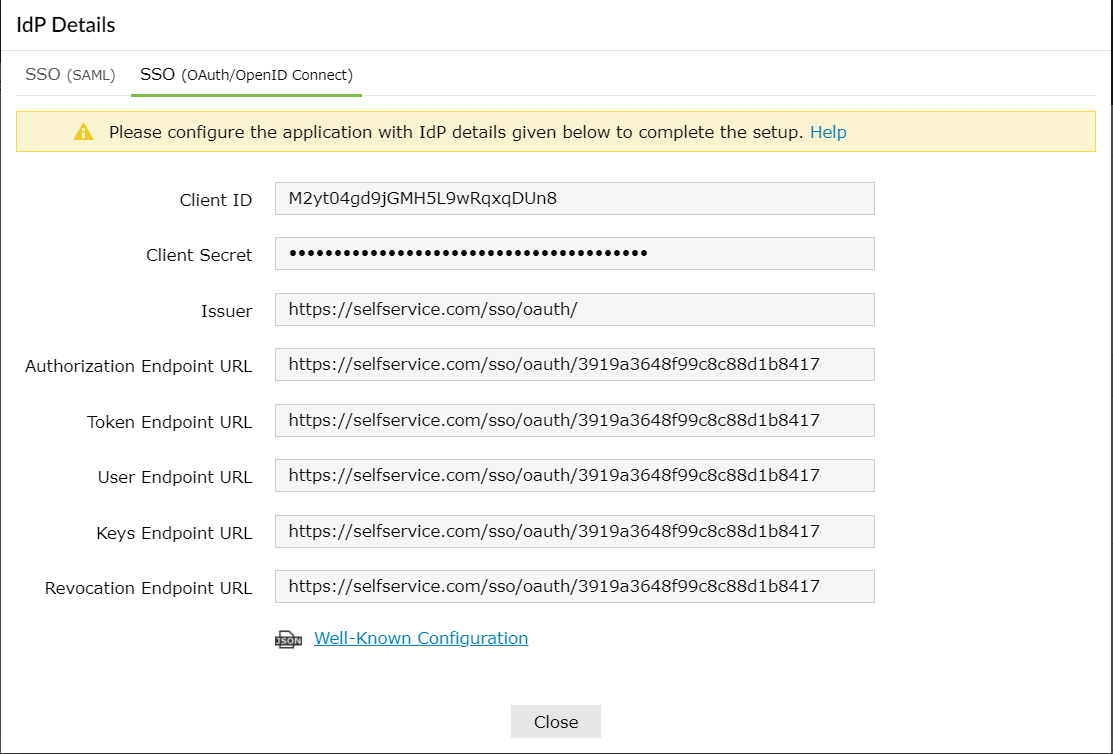
The Well-known Configuration URL in the IdP details pop-up contains all the endpoint values, supported scopes, response modes, client authentication modes, and client details. This is enabled only after you finish configuring the application for SSO in ADSelfService Plus. You can provide this to your service provider if required.
Copyright © 2025, ZOHO Corp. All Rights Reserved.