Technicians
Technicians are end users with specific privileges that allow them to carry out product-related administrative tasks. To log in to the ADSelfService Plus portal and perform administrative tasks, technicians need to be assigned an ADSelfService Plus license. The Technician Settings report (Configuration > Administrative Tools > Technician) enables you to monitor the licenses assigned to technicians from the Licensing Status column, which shows the licensing status of each technician.
- Domain-based Technicians: These are technicians who have an account in AD. Domain-based technicians only have control over the domain to which they belong.
- Product-based Technicians: These technician accounts are created in ADSelfService Plus and use their product account credentials for authentication. Product-based technicians have control over all the domains configured in ADSelfService Plus.
Technicians can be assigned one of these roles:
- Super Admin: Has full control over the entire application by default.
- Operator: Can audit operations and view reports in the application by default.
Note: You can configure MFA and password policy settings for product-based technicians using the Advanced settings in the Technicians tab. To do so, go to Configuration > Administrative Tools > Technician > Advanced. To configure MFA and password policy settings for domain-based technicians, go to Configuration > Self-Service > Multi-factor Authentication and Configuration > Self-Service > Password Policy Enforcer.
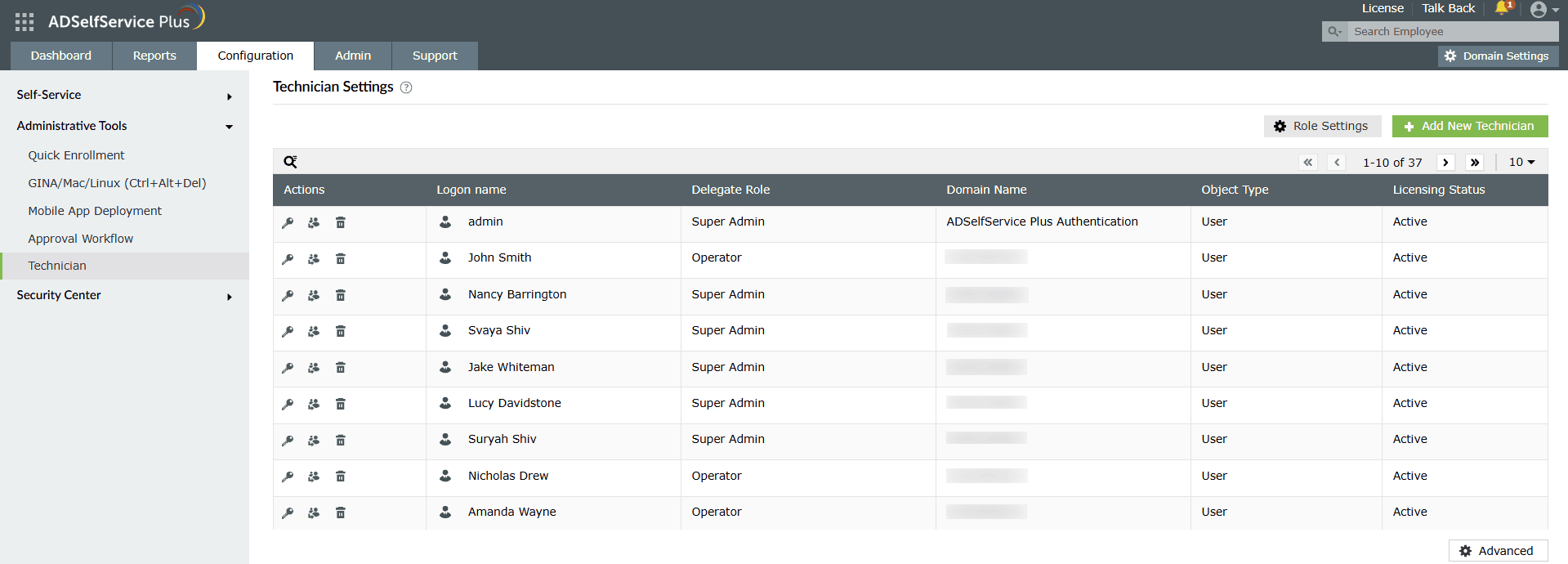
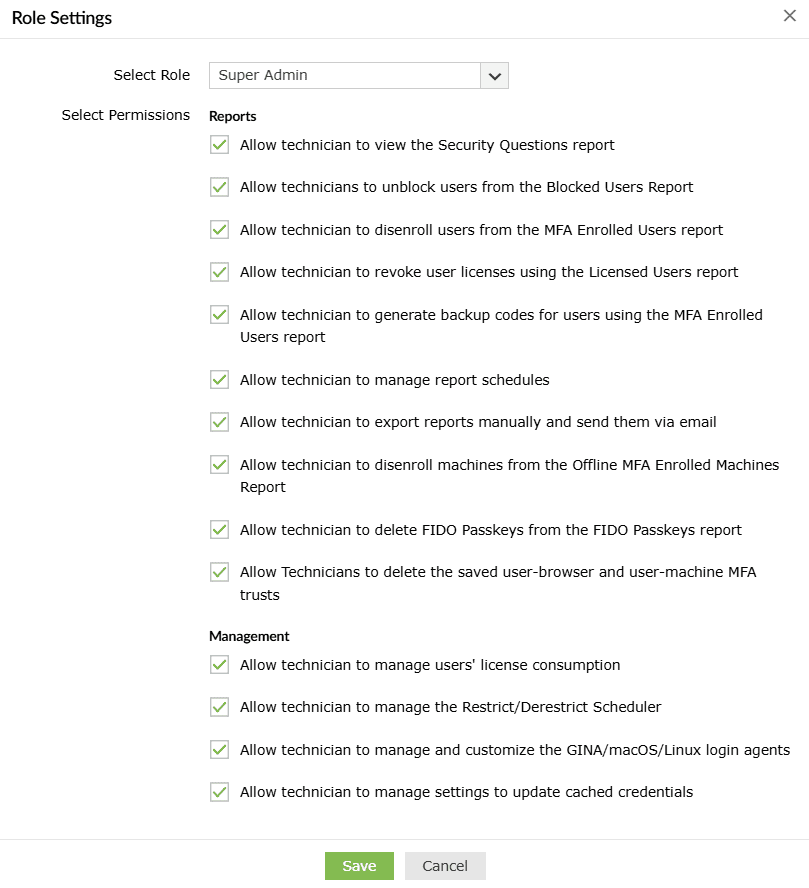
How to assign permissions to technician roles
- Go to Configuration > Administrative Tools > Technician..
- Click Role Settings.
- Select the required role from the drop-down.
- You can now choose to assign or remove the displayed permissions.
Note: If a product-based technician with the Super Admin role configures particular settings associating multiple domains or policies, any modifications to that setting will be replicated across the selected domains or policies. Domain-based technicians may make changes to these settings and be unaware of the implications since their visibility is restricted only to the domain they are part of. It is therefore recommended that product-based technicians configure settings affecting multiple domains or policies (mentioned below) only if absolutely required.
Configurations affecting multiple domains
- Azure AD MFA
- FIDO2 passkeys
- Duo Security
- RADIUS authentication
- SAML authentication
- YubiKey Authenticator
- Smart Card authentication
- Custom TOTP authenticator
- Password expiration notification
- Password sync/single sign-on
- Conditional access
- Self-update layout
- Employee search
- Manage custom attributes
- Data sources in import enrollment data from external database
- GINA/Mac/Linux customization
- Updating cached credentials over VPN
- APNs configuration (mobile app deployment)
In addition to these configurations, changes made by domain-based technicians to configurations in the Admin tab will also be replicated across other associated domains.
How to create a technician
- Go to Configuration > Administrative Tools > Technician.
- Click the + Add New Technician button.
- Select the technician type, role, domain, and users or groups from the respective drop-downs.
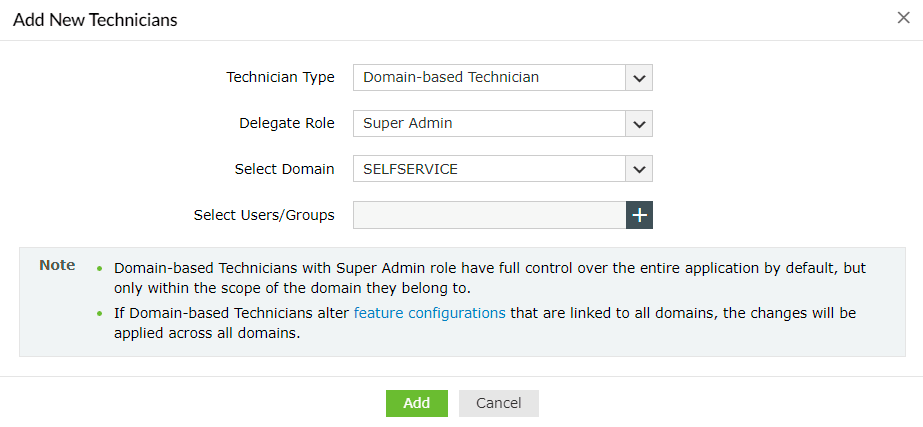
Important: When Domain-based Technician is selected, the created technician can use their Windows login credentials to log in to ADSelfService Plus.
- If you would like to allow the domain-based technician to manage local users, select the Delegate management of localuser.domain option
- If you select Product-based Technician in the Technician Type field, you will be required to enter the login credentials for that technician.
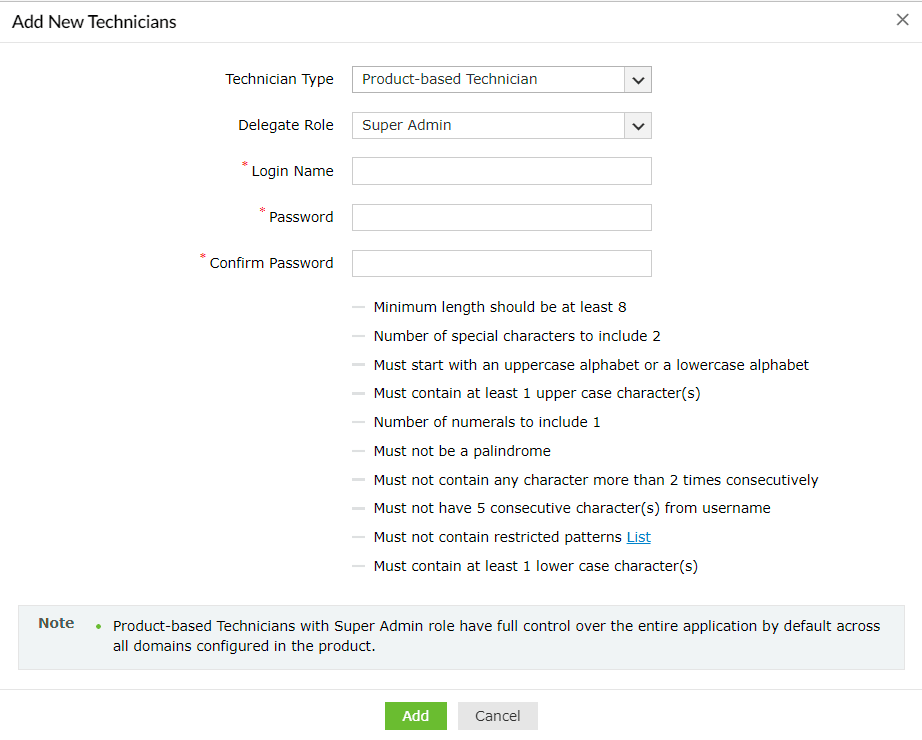
Important: When Product-based Technician is selected, this only creates an account in ADSelfService Plus. The technician will not have an AD account and needs to use the credentials that you configure to log in to the product.
- Click Add.
Advanced settings
The Advanced option on the Technician Settings page allows you to configure login MFA and password policy settings for technicians who use product authentication.
Login MFA
You can configure specialized MFA for technicians using this section.
- Go to Configuration > Administrative Tools > Technician.
- Click Advanced in the bottom-right corner and click the Login MFA tab.
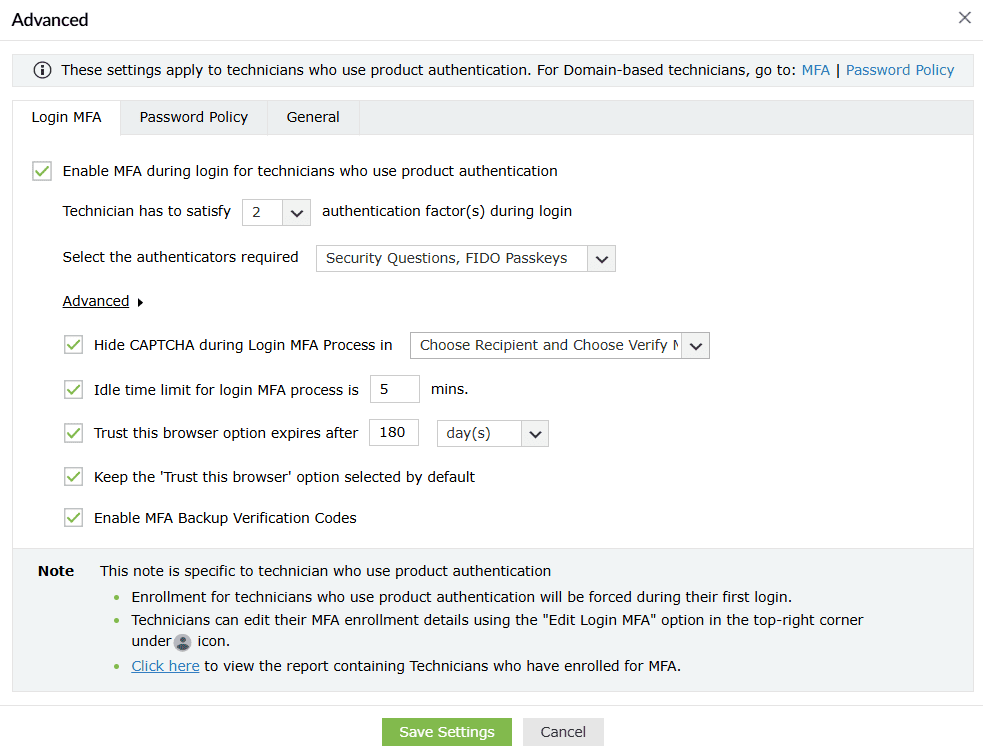
- Enable MFA during login for technicians who use product authentication: Enable this option if you want ADSelfService Plus to prompt product technicians for the configured MFA authenticators during login for additional security.
Note: These MFA settings will be applied to all product technicians, including the default administrator account. This will result in accounts without backup codes being locked out upon MFA failure. You can unblock the default admin account or contact support if the default administrator account is blocked.
If required, you can also choose to reset the default admin password using these steps.
- Technician has to satisfy __ authentication factor(s) during login: Choose the number of authenticators to prompt technicians for during login from the drop-down.
- Select the authenticators required: Choose the authenticators you wish to apply to the technician from the drop-down.
- Click Advanced to access more options to customize settings for technicians.
- Hide CAPTCHA during Login MFA Process in: Specify the MFA pages on which you do not want the CAPTCHA to be displayed.
- Idle time limit for login MFA process is__min: Specify the idle time limit for the login MFA process. Once the specified time has lapsed, if the technician failed to complete the verification process, they will have to go through the MFA verification process again.
- Trust this browser option expires after__: When this option is enabled, users will not be asked to go through MFA for the specified length of time when they log in to ADSelfService Plus using trusted browsers. Specify the duration of the trust period in days, hours, or minutes.
- Keep the 'Trust this browser' option selected by default: Enable this option if you want the Trust this browser check box to be selected by default on the MFA verification screen.
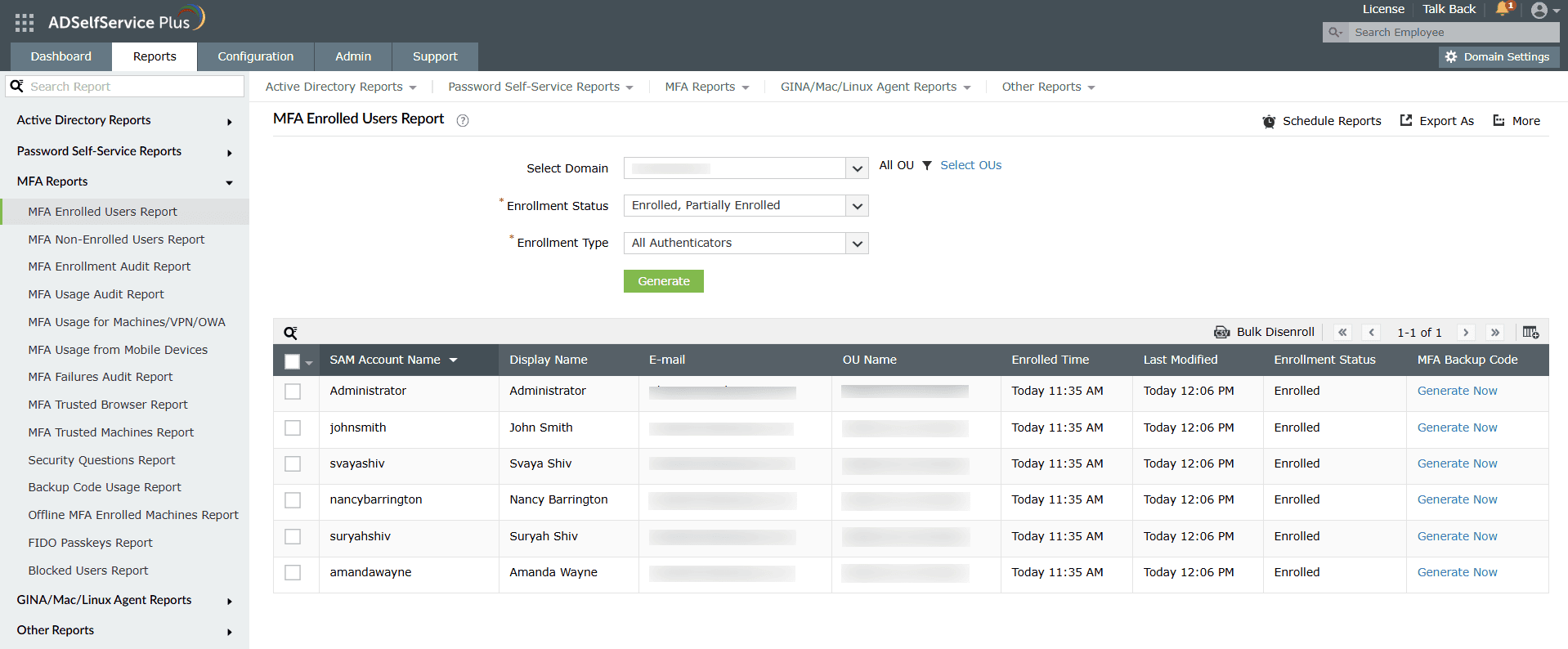
- Enable MFA Backup Verification Codes: Click this option to let admins generate backup codes for technician accounts via the MFA Enrolled Users Report. Admins can choose to display the MFA Backup Code column in the MFA Enrolled Users Report and generate backup codes from the report.
Password policy
- Go to Configuration > Administrative Tools > Technician.
- Click Advanced in the bottom-right corner and click the Password Policy tab.
- Restrict Characters: Specify how many special characters, numbers, and Unicode characters should be used in a password.
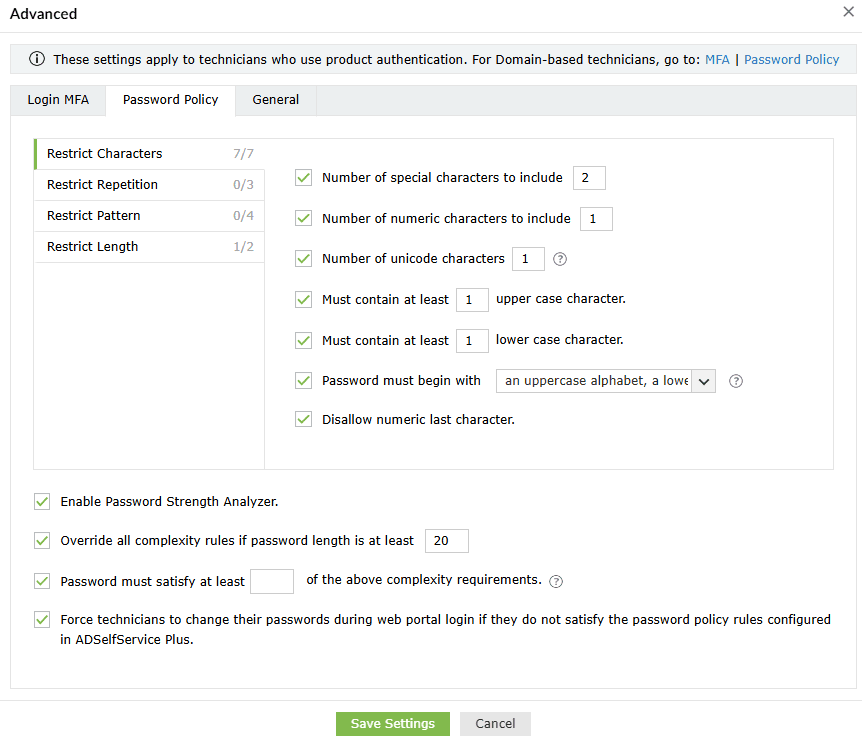
- Restrict Repetition: Limit the use of:
- Consecutive characters (e.g., aaaa).
- A string of consecutive characters from the username and old password (e.g. user01).
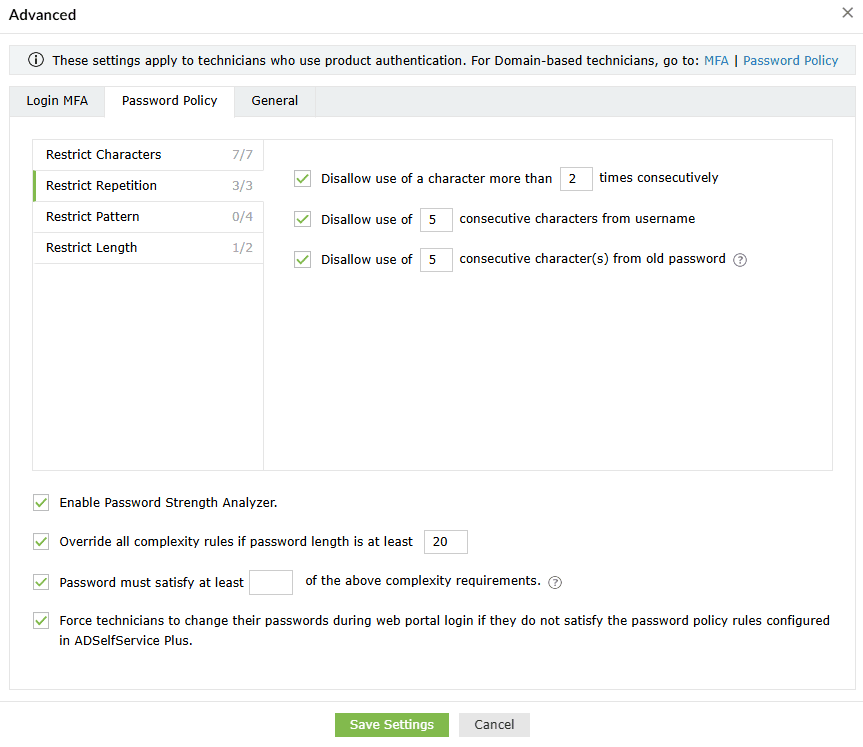
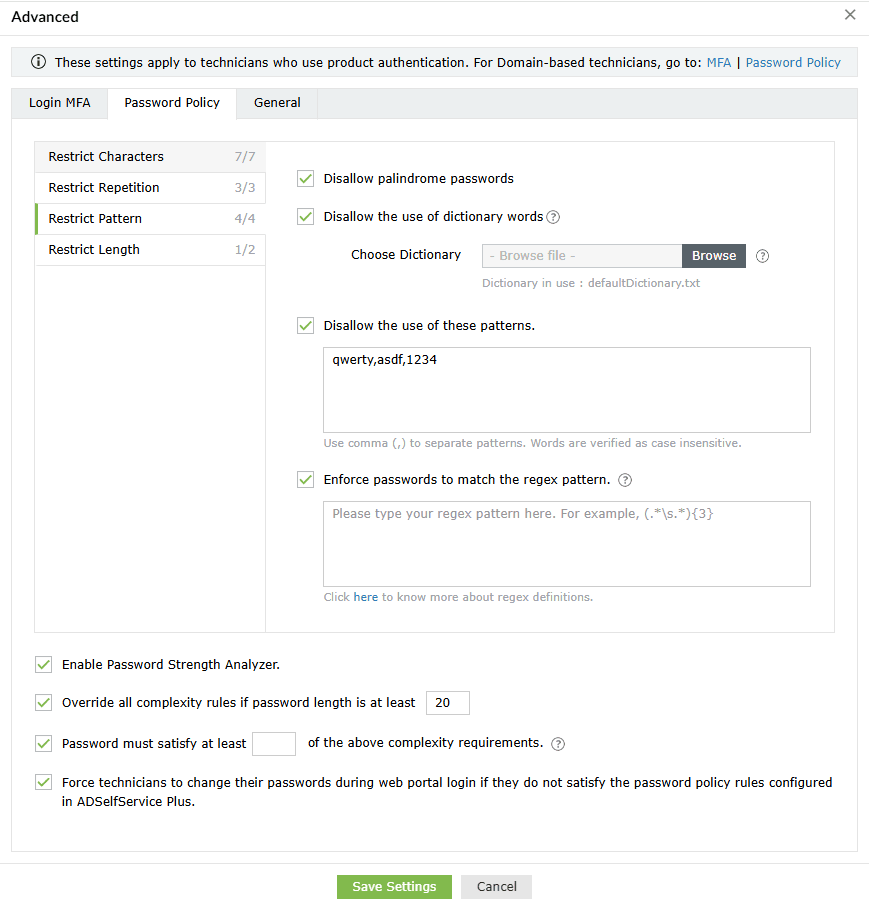
- Restrict Pattern: Restrict technicians from using keyboard sequences, dictionary words, and palindromes, or ensure that their passwords meet specific criteria by enforcing a regex pattern. Learn more about setting a regex pattern, here.
Important note: Ensure that the regex pattern and other password policy rules do not conflict with each other. If you enable a password policy based on a regex pattern, please ensure that the login agent on user machines is updated to version 6.11 or above, and the ADSelfService Plus app on technician devices is at least version 1.7.2 or 1.6.6 for Android or iOS devices, respectively.
- Restrict Length: Specify the maximum and minimum password length..
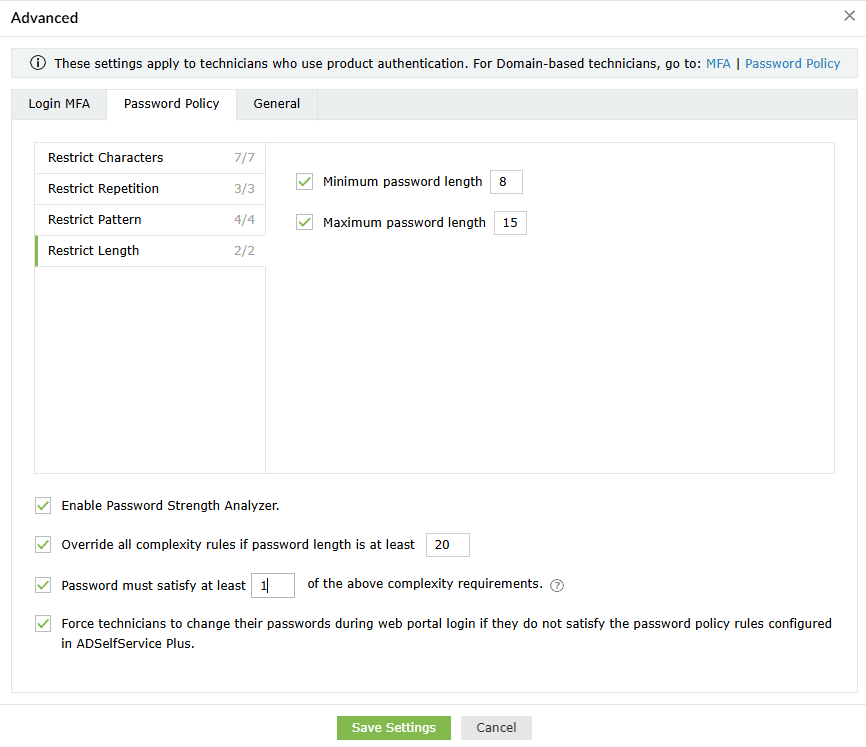
- Enable Password Strength Analyzer: Enable this setting to provide a visual representation of the strength of the password, encouraging technicians to create complex passwords.
- You can also configure the settings to Override all complexity rules if the password meets a predefined password length. You can also specify the number of complexity rules a password must satisfy.
- Secure technician accounts by verifying whether their passwords meet all the configured password policy rules in ADSelfService Plus and checking for compromised passwords usage through the Have I Been Pwned integration during each ADSelfService Plus portal login attempt. If the passwords do not satisfy the requirements, technicians will be forced to change them.
General
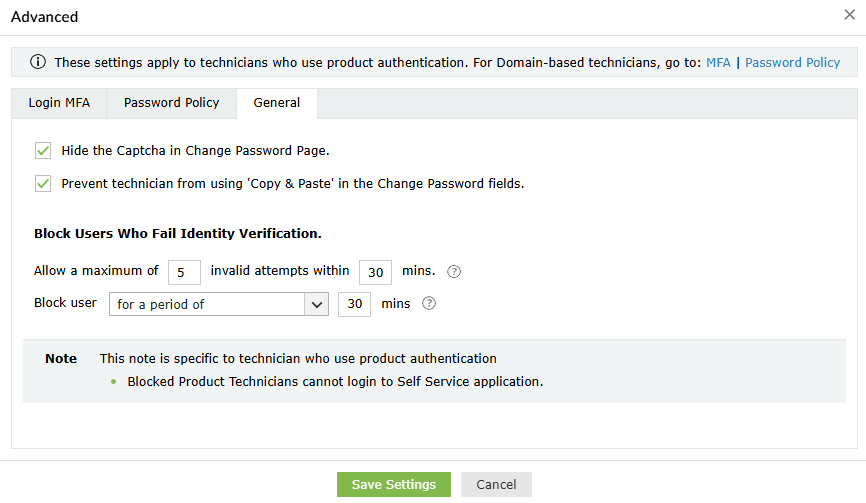
- Hide the CAPTCHA in the change password page: You can choose to hide the CAPTCHA on the change password page using this option.
- Prevent technician from copy-pasting the password in the change password fields: Ensure extra security by preventing technicians from copying and pasting passwords into password fields.
- Enable Password Strength Analyzer: Enable this option to help technicians analyze how strong their passwords are in real time when they reset or change their passwords.
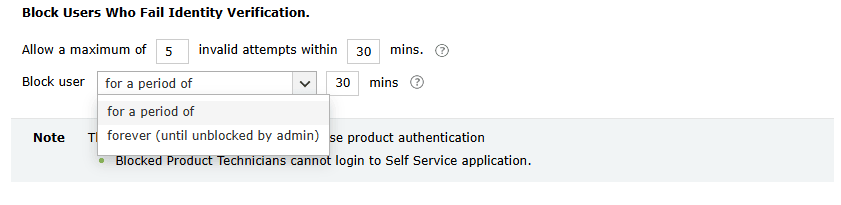
Block Users Who Fail Identity Verification
- Use the Allow a maximum of __ invalid attempts within __ mins option to define the maximum number of failed verification attempts allowed for a technician within a set time interval. Technicians who exceed the number of failed verification attempts specified here will be blocked.
Note: Each identity verification attempt failure, whether during password entry, backup code entry, or MFA verification, will count toward the maximum verification attempts limit before the account is blocked. Blocked users cannot reset passwords, unlock accounts, or log in to applications or endpoint devices.
MFA failures while using Duo Security or Smart Card Authentication will not be counted towards identity verification failures, as those authenticators have their own blocking mechanisms.
You can unblock the default admin account or contact support if the default administrator account is blocked.
If required, you can also choose to reset the default admin password using these steps.
- Using the Block user for a period of __ min option, specify:
- The number of minutes for which the technician will remain blocked.
Example: For instance, say you have set the maximum invalid attempts to be five, defined the time interval as 10 minutes, and specified the period for which the user will remain blocked as 30 minutes. This means that when a technician fails to verify their identity five times in a 10-minute interval, they will be blocked for 30 minutes.
- Choose Forever (until unblocked by admin) to configure technician accounts to remain blocked until manually unblocked by an admin. Blocked accounts can be unblocked from the Blocked Users Report.
Technicians who are blocked while trying to access applications or endpoints, or while performing self-service password resets or account unlocks, will be restricted from accessing every endpoint protected by ADSelfService Plus until their account is unblocked.












